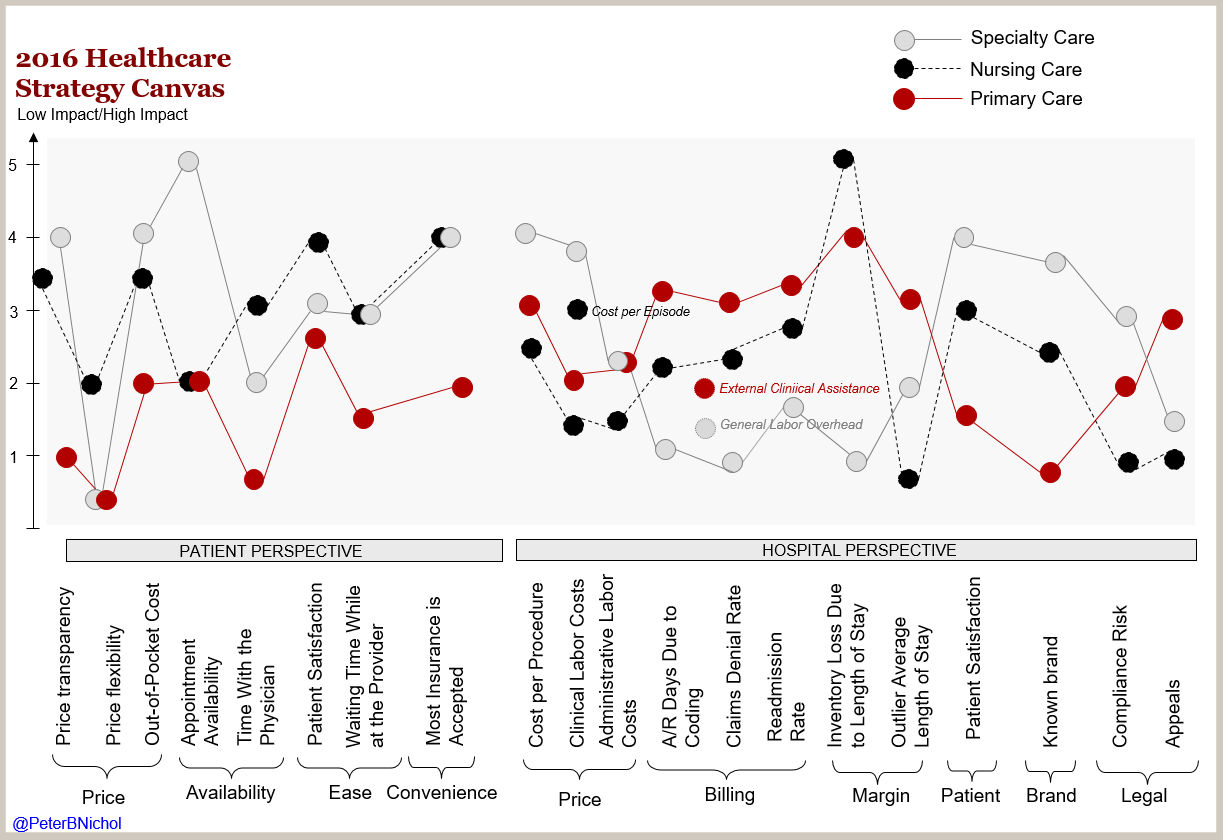
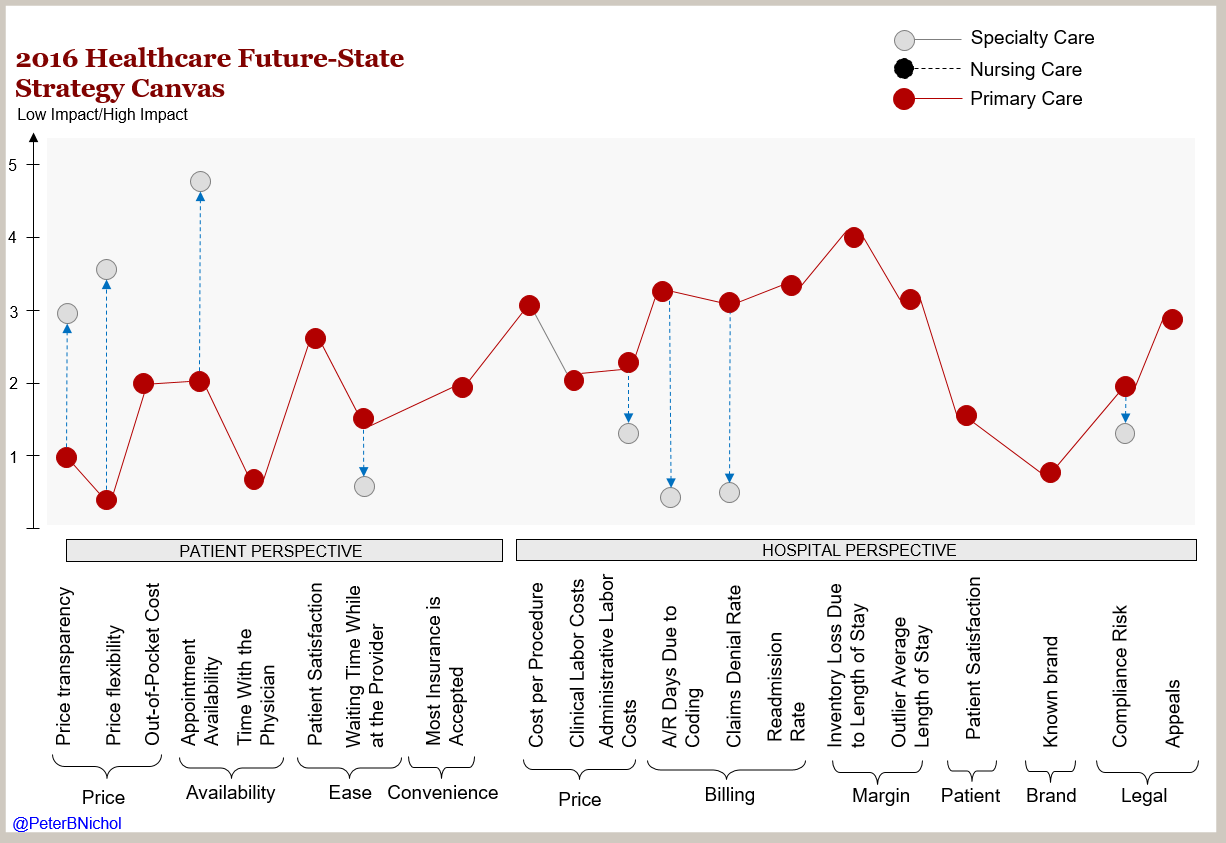
Your daily habits could be interrupted by connected systems enabling access to new processing paradigms. Information processing systems inspired by biological nervous systems may change your diagnosis.
We’re supposed to eat less, work out more and use less salt. These goals rarely materialize into a productive pattern. Our behavior doesn’t change. Even with the incredible amount of information available, we choose not to change.
Artificial neural networks (ANN) have the ability to influence medical diagnoses and change our behavior. Change is more than what you should or shouldn’t do. How you connect data and squeeze out information also impacts our ability to change.
Artificial neural networks forecasting our health
Artificial neural networks have a wide range of uses in science and technology with applications across chemistry, physics and biology. The simulation of neural networks has been used to enhance group tactics for playing soccer, fighting crime, accelerating facial image processing and expanding nanotechnology.
Artificial neural networks can address nonlinear problems by mapping multidimensional data sets into two-dimensional spaces. They “learn” based on input and outputs as information flows through the network. The flow of information changes the structure of the artificial neural network. These networks evolve independently.
Classifications of neural networks
Connecting things adds value. The TV doesn’t do much good without power. It’s helpful to know your iPhone data is backed up with cloud storage. Spending money can get you fed at a restaurant.
Usually, we think of combining physical things to create more value. However, the greatest value gains have nothing to do with physical objects; they have everything to do with combining data to form new information. This information has value and forms the utility of artificial neural networks. They combine data into information we’d otherwise never have created.
The key to understanding artificial neural networks begins by identifying the types of artificial neural network we’re talking about. There are four main classifications of neural networks, within a field where over 50 types exist.
- Dynamic neural network: networks that either form or do not form a cycle.
- Static neural network: networks with no context memory.
- Memory network: networks with context memory.
- Other types of networks: networks that operate similar to neuronal (mathematical functions) and synaptic states (linking neurons) with the additional feature that these networks also incorporate the concept of time into their operating model.
The challenges of scientists
Scientists and technologists have long had an interest in neural networks. Cognitive science, parallel processing, control theory, neurophysiology, physics, artificial intelligence and computer science all must merge to form the base of knowledge to design, construct and implement artificial neural networks. This field challenges scientists to address the following problems:
- Pattern classification: divide the items into categories and then identify those patterns.
- Clustering and categorization: unsupervised pattern classification with no training, by identification of similar patterns.
- Functional approximation: the function is tasked to find an estimate or the unknown value through various engineering and modeling techniques.
- Prediction and forecasting: uses a time sequence data set predict a sample to help make decisions typically in business or science.
- Optimization: identifies a solution given a set of constraints for problems in science, medicine or economics.
- Content-addressable memory: the address of memory is the same or separate from the contents and content in memory and can be recalled even by partial input to show context.
- Control: the model generates a control input, so the system follows a desired trajectory based on a reference model.
Let’s make these problems more practical. Pattern classification could be used to identify abnormal EEG wave forms or for character recognition, speed recognition or blood cell classification. Clustering and categorization could identify high versus low risk populations based on blood or DNA samples. Functional approximation may help a patient decide to either have surgery or explore nonsurgical options (decision support). Prediction and forecasting, using nonlinear regression computational techniques, could aid in new drug discoveries, identification of regenerative medicine, or determine what effect that shake of salt will have on your lifespan.
Optimization can be used to minimize an objective function, e.g. swarm intelligence or robots working in a team for uniform interactions or movement. Content-addressable memory could be used for vision and pattern recognition, in combination with a learning algorithm to identify how viruses may mutate, helping the early discovery of cures. Control could be used to correct motion control problems in industrial applications, vehicles and surgical robots.
Connectionist models of survival
These models are especially applicable when predicting survival after the diagnosis of a rare disease. Would it matter if you knew you had 20 years left and not two months? It would matter to me.
It’s science that transcends from the cliff of innovation to the plateau of practicality.
Using artificial neural networks, combined with machine learning, medicine survival analysis can be calculated. Diagnosis, treatment-response forecasting and outcome predictions are just a few of the capabilities neural networks have demonstrated. Artificial neural networks may soon help change your behavior.
Peter B. Nichol, empowers organizations to think different for different results. You can follow Peter on Twitter or his personal blog Leaders Need Pancakes or CIO.com. Peter can be reached at pnichol [dot] spamarrest.com.
Peter is the author of Learning Intelligence: Expand Thinking. Absorb Alternative. Unlock Possibilities (2017), which Marshall Goldsmith, author of the New York Times No. 1 bestseller Triggers, calls “a must-read for any leader wanting to compete in the innovation-powered landscape of today.”
Peter also authored The Power of Blockchain for Healthcare: How Blockchain Will Ignite The Future of Healthcare (2017), the first book to explore the vast opportunities for blockchain to transform the patient experience.